Azure DevOps Logs & Auditing
Using Log Parser Lizard and the public preview of Azure DevOps Auditing to analyse logs.

As of October 2019, Azure DevOps auditing is in public preview, so what is said below might be wrong in a while...but lets carry on anwyay!
Permissions
By default, Project Collection Administrators are the only group that can access the auditing feature. For everyone else you need to be given permission to view the logs.
Go to your Organisation Settings.
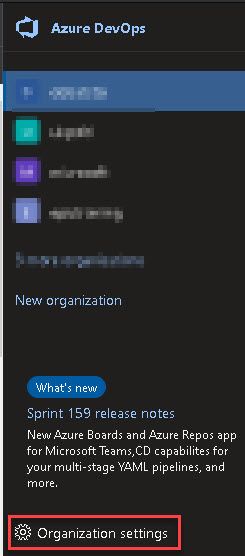
Click Permissions under the Security heading.
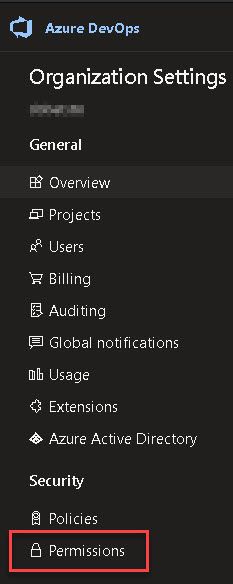
Once in the permissions screen, choose a group or individual user to edit. You will find (at the time of writing) that the "View Audit Log" is right at the bottom but if it isn't there have a look around the screen because in typical Microsoft style it moves from time to time!
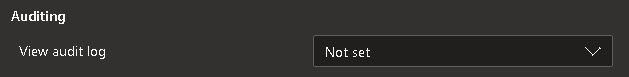
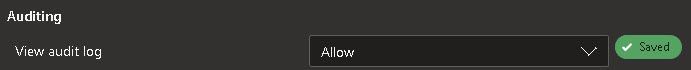
When you change the dropdown value, it will automatically save your new choice.
Getting to the logs
Now that we have permission we can go and get the logs. These are at the Organisation level, so just click "Auditing" from the menu on the left. You'll load a screen where there is "nothing to see here". If you notice the date range in the top-right of the screen will be set to todays date. It is curently only in the USA date format (at least for the preview).
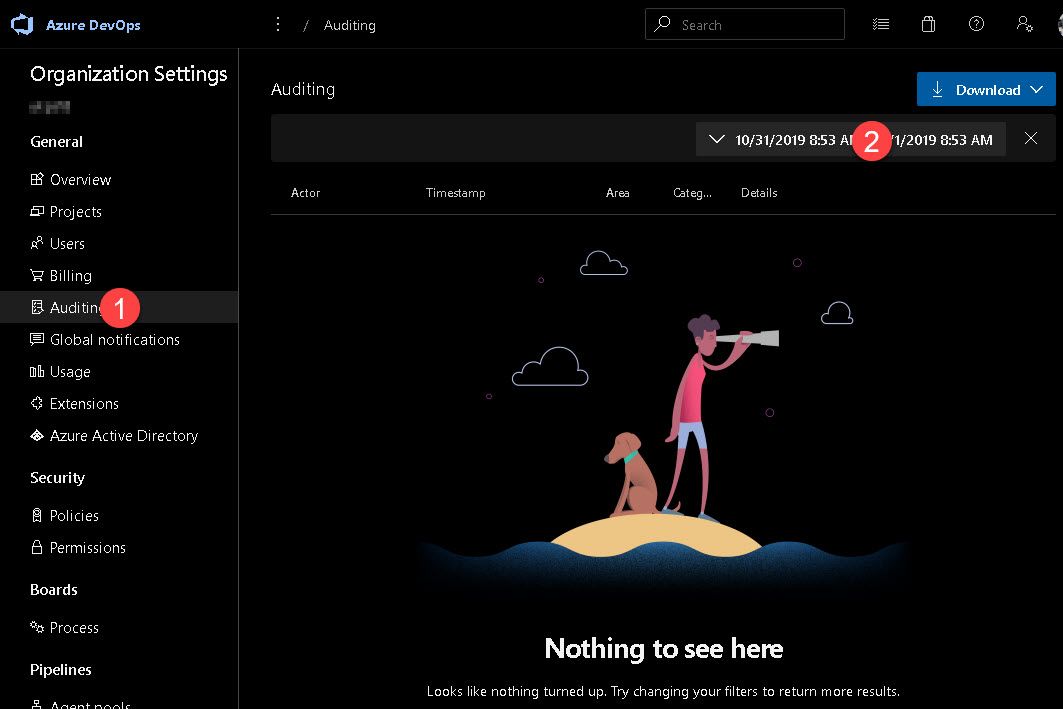
The results show what people have been doing but also Azure DevOps itself in the column Actor (#1). Also, under the persons name is the IP address of where the action occured. The Details column (#2) shows what has been done and occassionally you see a small (i) icon (#3) which when clicked will show further details. In this case it shows the three dates mentioned in the Details of that row.
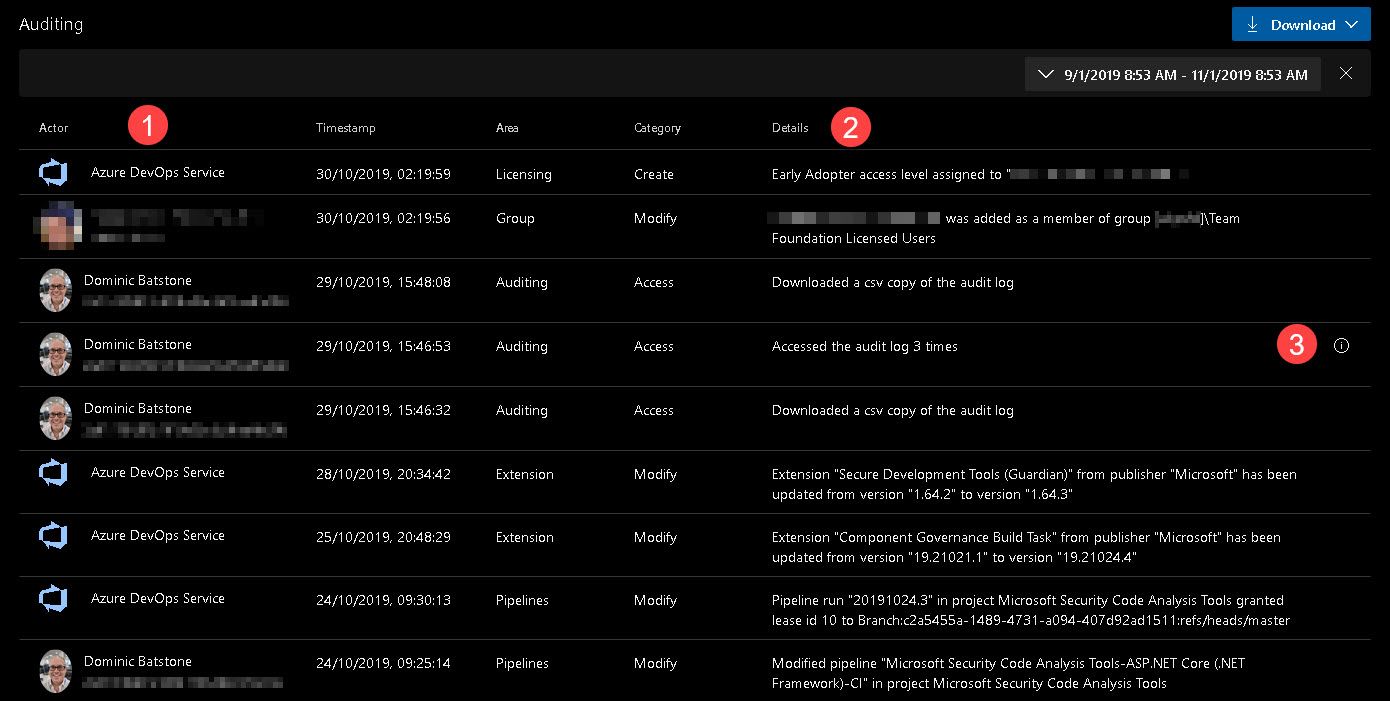
Click the download button to download a CSV of the data in your date range. If you read the CSV you'll see that each audit event has a unique identifier called the “ID” and a correlation ID called the “CorrelationID”. The correlation ID is helpful to find related audit events. For example, a project creation can generate several dozen audit events. You can link these events together because they all have the same correlation ID.
When an audit event ID matches its correlation ID, that’s an indication that the audit event is the parent or original event. So, the initial event, showing that a user created a project, will have the same ID as the correlation ID.
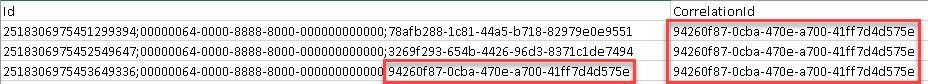
If you want to view only the set of events that were originators and not post action events, you can set a filter for where “ID” equals the “Correlation ID”. Then, if you find an event that you’re interested in investigating, you can search for just events with that correlation ID. Note that not all events have other related events.
The following limitations exist for what can be audited.
- Azure Active Directory (Azure AD) group membership changes – In the future, auditing will include changes to Azure DevOps groups, such as adding or removing a group or user. However, if you manage membership via Azure AD groups, additions and removals of users from those Azure AD groups are not audited by Azure DevOps. Review the Azure AD audit logs to see when a user or group was added or removed from an Azure AD group.
- Signing in – Sign-in events to Azure DevOps aren't tracked. View the Azure AD audit logs to review sign-in events to your Azure AD.
(Source: https://docs.microsoft.com/en-us/azure/devops/organizations/settings/azure-devops-auditing?view=azure-devops )
Unleashing Log Parser Lizard
Readers will know that my favourite log parsing tool for the past few years is the awesome Log Lizard which builds on top of the command line tool Log Parser. You might want to check-out one of my older posts the have a few queries you can learn from. See Lizard about with Log Lizard part 1.
You can see from this query that it is excluding all the rows created by the "Azure DevOps Service".
SELECT
substr(TimeStamp,0,10) AS Date,
substr(TimeStamp,11,8) AS Time,
ScopeType,
ProjectName,
IPAddress,
Area,
Category,
ActorDisplayName,
Details,
TO_TIMESTAMP(TimeStamp,'dd/MM/yyyy hh:mm:ss') AS LocalTime
FROM <path to your CSV>
WHERE ActorDisplayName <> 'Azure DevOps Service'
ORDER BY LocalTime DESCThis query will show what people have been doing. You can see that I have been adding fields to our teams Agile template. Also, users & permissions have been changing for certain users.
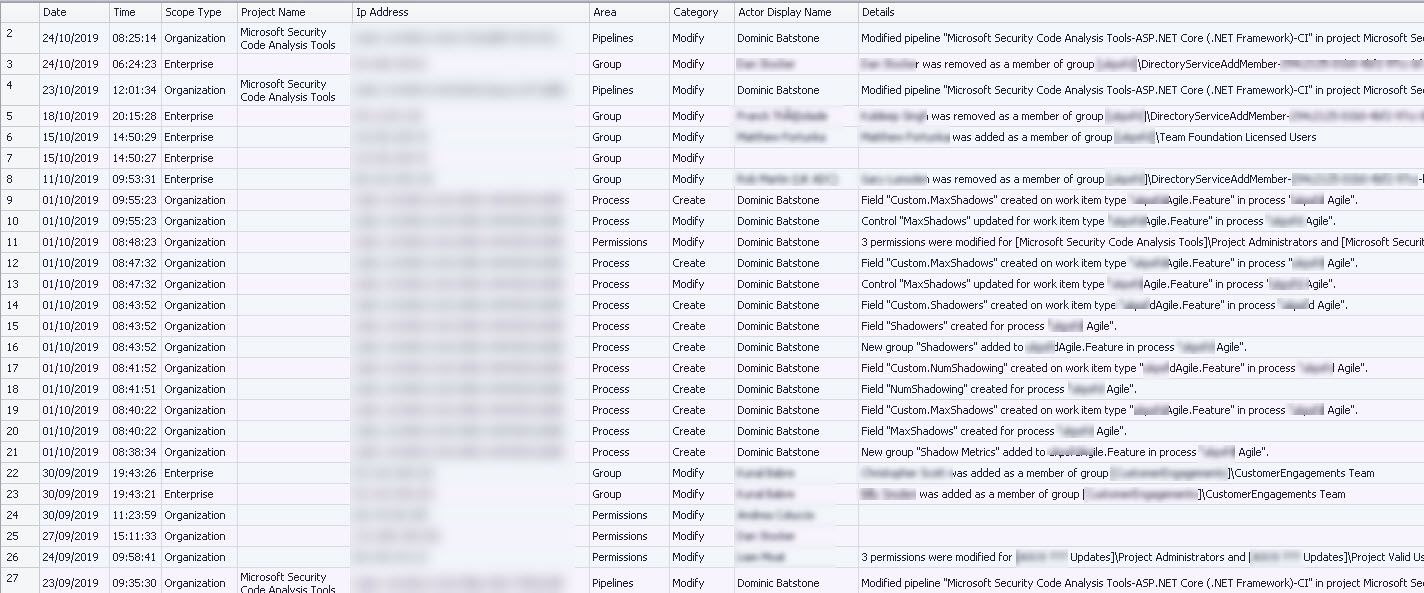
Of course you could start by Grouping By CorrelationID to see what was happening for a single event
SELECT CorrelationId,
substr(TimeStamp,0,10) AS Date,
substr(TimeStamp,11,8) AS Time,
Details,
TO_TIMESTAMP(TimeStamp,'dd/MM/yyyy hh:mm:ss') AS LocalTime
FROM <path to your data>
WHERE ActorDisplayName <> 'Azure DevOps Service'
AND strlen (Details) > 0
AND
CorrelationId IN (SELECT CorrelationId
FROM <path to data>
GROUP BY CorrelationId
HAVING Count(CorrelationId) > 1)
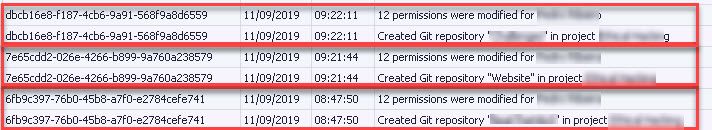
ORDER BY LocalTime, CorrelationId DESCSo here we can see that one of my colleagues was in quick succession creating multiple projects with associated permissions.
More Resources:
